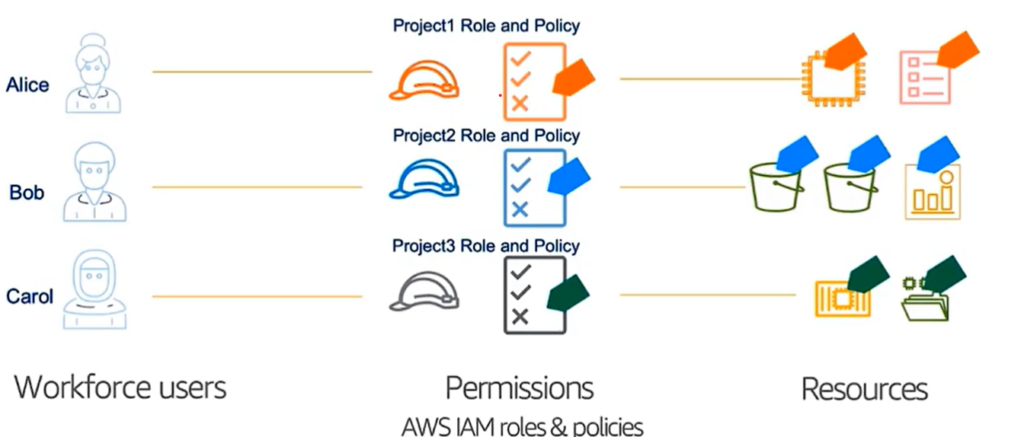
In the ever-evolving landscape of cloud computing, secure resource sharing across accounts is paramount. AWS simplifies this process with AWS Security Token Service (STS) and AssumeRole, enabling federated authentication. This method eliminates the need for long-term credentials while ensuring robust access controls.
In this blog, we’ll explore how AssumeRole enables secure cross-account access, the best practices to follow, and step-by-step instructions to implement it seamlessly.
What Is Federated Authentication with AssumeRole?
Federated authentication in AWS allows users or applications in one account (source) to access resources in another account (destination) without storing permanent credentials. Instead, temporary security credentials are issued via the AssumeRole API, providing:
- Enhanced Security: No static access keys to manage or rotate.
- Temporary Access: Credentials expire automatically, reducing exposure risk.
- Fine-Grained Control: Permissions are scoped to specific actions and resources.
Key Benefits of Using AssumeRole for Cross-Account Access
- Centralized Access Management: Simplify administration by managing roles in the destination account while enabling multiple source accounts to access resources.
- Dynamic Credential Issuance: Credentials are valid for a limited time (default: 1 hour, max: 12 hours), reducing misuse risks.
- Audit and Monitoring: All AssumeRole activities are logged in AWS CloudTrail, offering complete visibility for compliance and security audits.
How to Implement AssumeRole for Secure Federated Access
Step 1: Create a Role in the Destination Account (Account B)
- Log into Account B and navigate to the IAM Console.
- 2. Create a New Role:
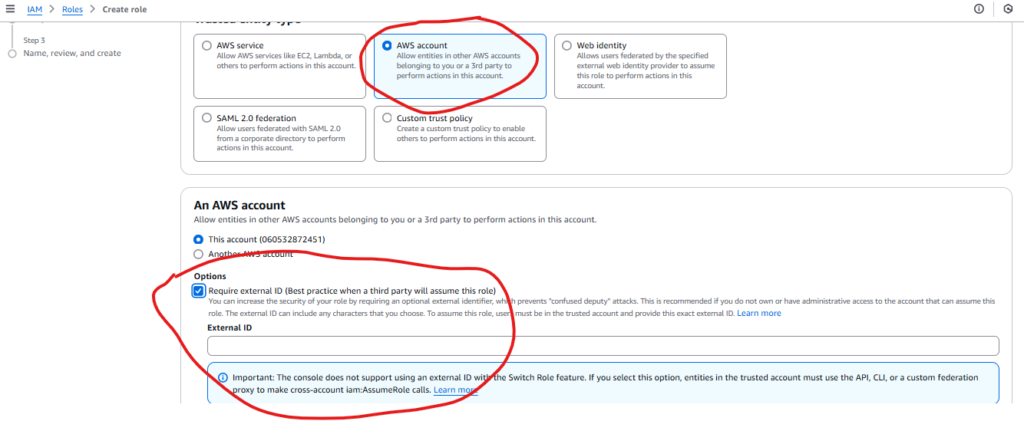
- Choose AWS Account as the trusted entity.
- Enter the Account ID of Account A (source account).
- Optionally, set an External ID for enhanced security.
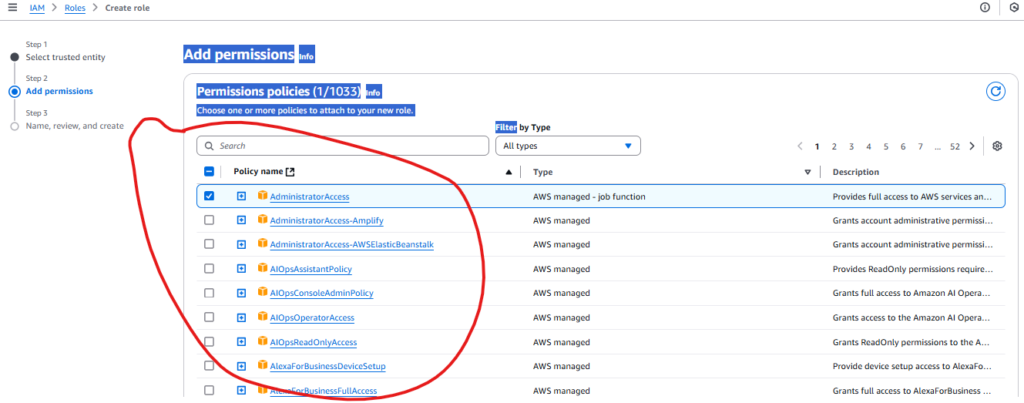
- 3. Attach Policies: Grant specific permissions required for the task (e.g., access to an S3 bucket or DynamoDB table). Avoid broad permissions like
AmazonS3FullAccess.
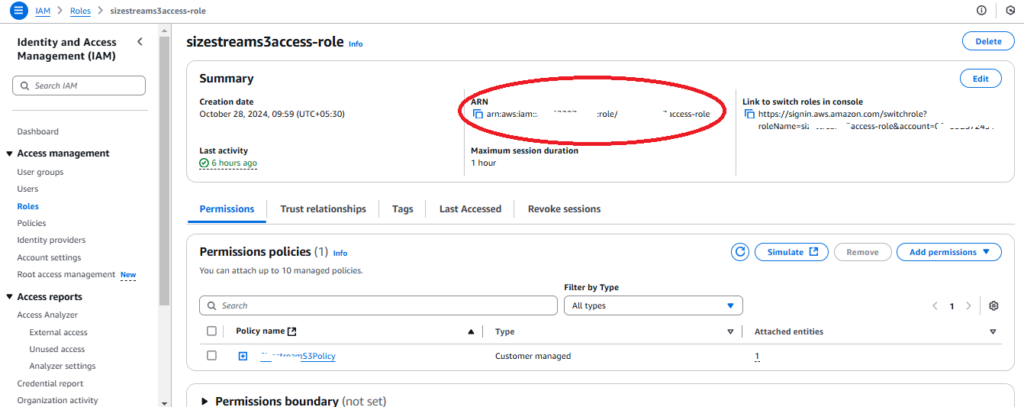
- 4. Copy the Role ARN: Save the ARN for configuration in Account A.
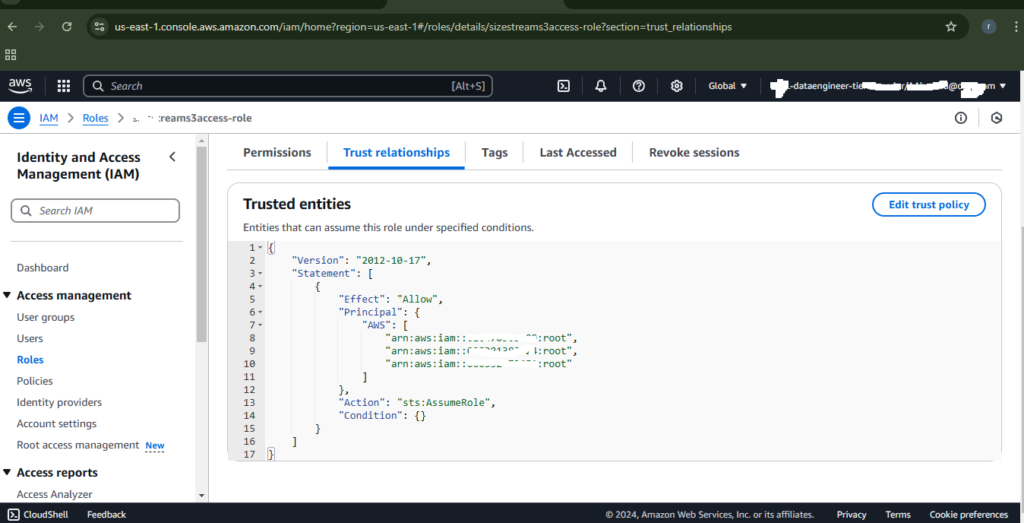
Step 2: Configure Trust Policy in the Destination Role
Update the trust policy in Account B to allow Account A to assume the role:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::AccountAID:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "YOUR_EXTERNAL_ID"
}
}
}
]
}
Step 3: Set Up Permissions in the Source Account (Account A)
- Attach a policy to the user or role in Account A that will assume the role in Account B. Example policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::AccountBID:role/DataDumpRole"
}
]
}Step 4: Programmatically Assume the Role
Use the AssumeRole API in Account A to generate temporary credentials and access Account B’s resources.
Example in Python with boto3:
import boto3
# Initialize STS client
sts_client = boto3.client('sts')
# Assume the role in Account B
response = sts_client.assume_role(
RoleArn="arn:aws:iam::AccountBID:role/DataDumpRole",
RoleSessionName="CrossAccountSession",
ExternalId="YOUR_EXTERNAL_ID"
)
# Extract temporary credentials
credentials = response['Credentials']
# Use temporary credentials for an S3 operation
s3_client = boto3.client(
's3',
aws_access_key_id=credentials['AccessKeyId'],
aws_secret_access_key=credentials['SecretAccessKey'],
aws_session_token=credentials['SessionToken']
)
# Upload a file to an S3 bucket in Account B
s3_client.put_object(Bucket='destination-bucket', Key='example-key', Body='example-data')Best Practices for Federated Authentication
- Use External IDs: Protect against confused deputy attacks by requiring an External ID for AssumeRole.
- Restrict Permissions: Grant only the permissions necessary for the task. For example, allow
s3:PutObjectfor a specific bucket. - Monitor Activity: Use CloudTrail to log and monitor AssumeRole API calls.
- Enable Logging: Configure logging on resources like S3 to track data access and operations.
- Automate Credential Refresh: Since temporary credentials expire, implement automated refresh mechanisms.
Federated authentication with AssumeRole is a secure and efficient way to manage cross-account access in AWS. By following the outlined steps and best practices, you can eliminate the risks of long-term credentials, streamline resource sharing, and maintain robust security controls.
Adopting this approach not only reduces operational complexity but also ensures compliance with modern security standards. Begin leveraging AssumeRole today to unlock seamless cross-account collaboration in AWS! You might also like this: How to Get Access Key and Secret Key in AWS.