AWS S3 is a widely used cloud storage service, and setting up Cross-Account Replication is an essential feature for redundancy, disaster recovery, or compliance. This blog will guide you through the process in simple steps.
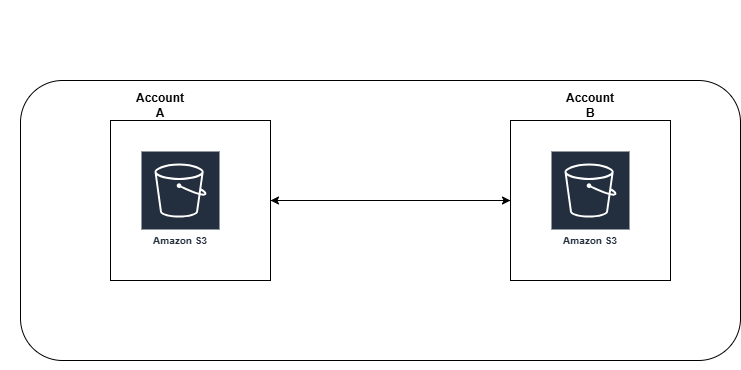
What Is Cross-Account S3 Replication?
Cross-Account Replication lets you automatically copy objects from a source bucket in one AWS account to a destination bucket in another AWS account. It’s a great way to ensure your data is safely stored in another account, providing fault tolerance and additional security.
Why Use Cross-Account Replication?
- Data Backup: Protects data in case of accidental deletion or corruption.
- Compliance: Stores data in separate accounts for regulatory or legal reasons.
- Data Sharing: Shares data securely between different teams or organizations.
Prerequisites
Before starting, ensure the following:
- A source bucket in Account A and a destination bucket in Account B.
- Versioning is enabled for both buckets.
- The destination bucket has the necessary permissions.
- If you use Object Lock, ensure the feature is enabled on the destination bucket.
Step-by-Step Guide
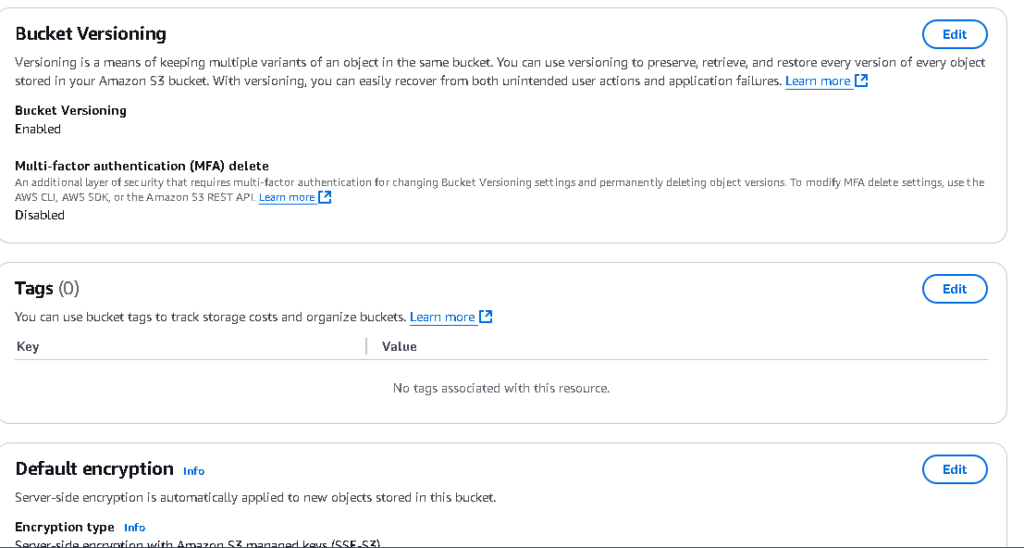
Step 1: Enable Bucket Versioning
- Go to the AWS Management Console.
- Navigate to the S3 service and select your source bucket.
- Under the Properties tab, enable Versioning.
- Repeat these steps for the destination bucket.
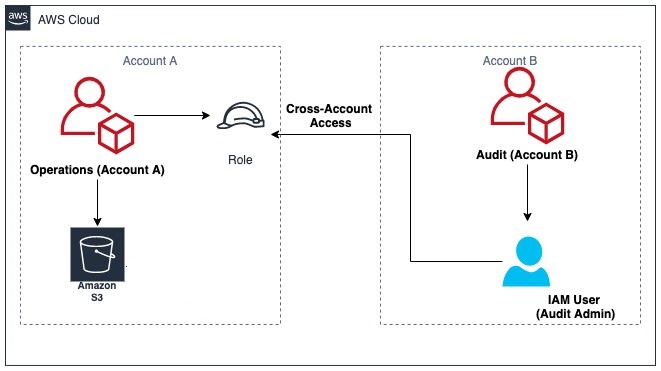
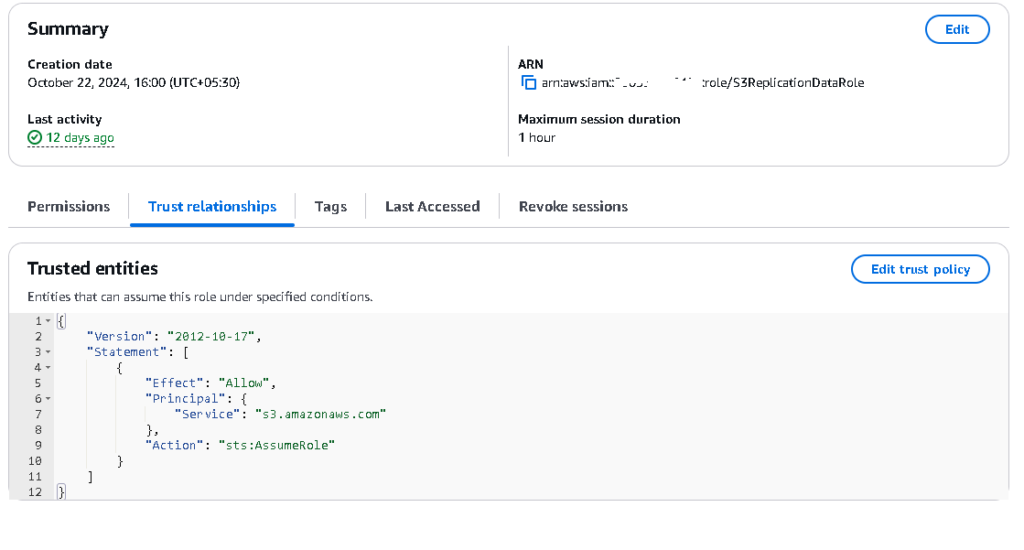
Step 2: Set Up IAM Role in the Source Account
- Open the IAM Console in Account A (Source Account).
- Create a new role and choose S3 as the trusted service.
- Add the following trust policy for Amazon S3:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
4. Attach the required permissions to the role. Example policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SourceBucketPermissions",
"Effect": "Allow",
"Action": [
"s3:GetObjectRetention",
"s3:GetObjectVersionForReplication",
"s3:ListBucket",
"s3:GetReplicationConfiguration"
],
"Resource": [
"arn:aws:s3:::SourceBucketName/*",
"arn:aws:s3:::SourceBucketName"
]
},
{
"Sid": "DestinationBucketPermissions",
"Effect": "Allow",
"Action": [
"s3:ReplicateObject",
"s3:ReplicateDelete",
"s3:ReplicateTags"
],
"Resource": [
"arn:aws:s3:::DestinationBucketName/*"
]
}
]
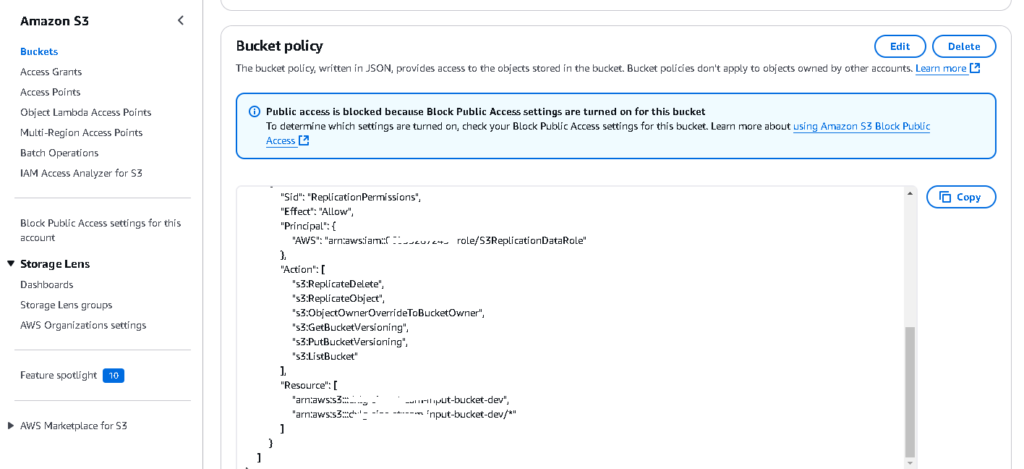
}Step 3: Add Bucket Policy to the Destination Bucket
- Open the S3 Console in Account B (Destination Account).
- Select the destination bucket and go to the Permissions tab.
- Add the following bucket policy to grant the source account permission:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ReplicationPermissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::SourceAccountID:role/ReplicationRoleName"
},
"Action": [
"s3:ReplicateObject",
"s3:ReplicateDelete",
"s3:GetBucketVersioning",
"s3:PutBucketVersioning"
],
"Resource": [
"arn:aws:s3:::DestinationBucketName/*",
"arn:aws:s3:::DestinationBucketName"
]
}
]
}
Replace:
SourceAccountIDwith the source account’s ID.ReplicationRoleNamewith the IAM role name created earlier.DestinationBucketNamewith the name of your destination bucket.
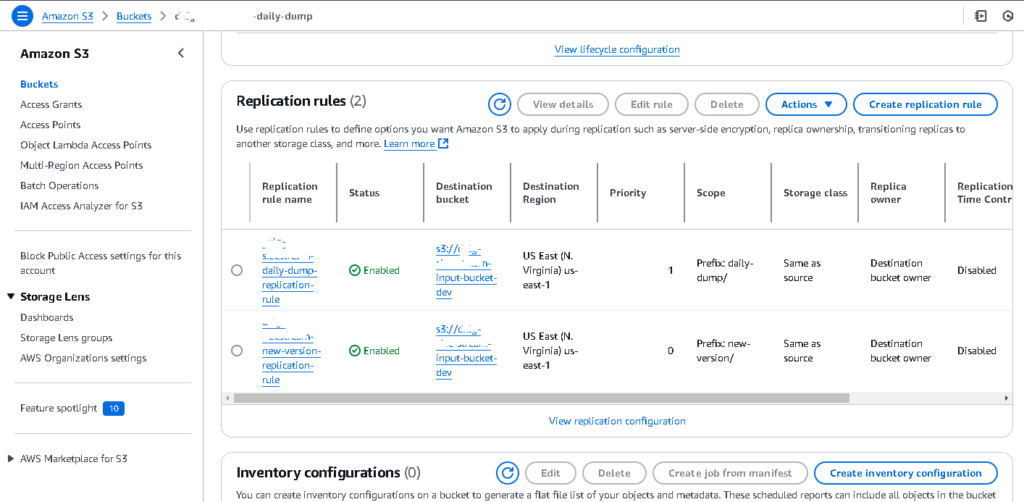
Step 4: Set Up Replication Rule in the Source Bucket
- Open the S3 Console in Account A.
- Select the source bucket and navigate to the Management tab.
- Click on Replication rules > Create replication rule.
- Configure the rule:
- Rule Name: Enter a meaningful name (e.g.,
CrossAccountReplication). - Destination: Choose Bucket in another account and provide the destination bucket name and account ID.
- IAM Role: Select the IAM role created earlier.
- Rule Name: Enter a meaningful name (e.g.,
- Review the settings and save the rule.
Step 5: (Optional) If Using AWS KMS Encryption
If the buckets use AWS KMS keys for encryption, ensure proper permissions:
- Update the KMS key policy for both accounts to allow access to the replication role. Example for the destination bucket’s KMS key:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowReplicationRoleAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::SourceAccountID:role/ReplicationRoleName"
},
"Action": [
"kms:Encrypt",
"kms:GenerateDataKey"
],
"Resource": "*"
}
]
}Step 6: Test the Setup
- Upload a test object to the source bucket.
- Check the destination bucket to ensure the object is replicated.
- Verify the replication status in the source bucket’s Management tab.
Common Issues and Tips
- Permission Errors: Double-check IAM roles, bucket policies, and KMS key policies.
- Replication Delays: Replication is asynchronous, so it might take a few minutes.
- Existing Objects Not Replicated: Replication applies only to new objects after the rule is created.
Cross-account S3 replication is a robust solution for ensuring data availability and compliance. By following these steps, you can set it up confidently and securely. If you encounter challenges, AWS documentation and support are always available to help!


